The news section of social media channels has been flooded with images that might have come from Gaza or Israel. Public outcry about generative AI fakes is not new but there has been a burst of questionable content just before and during the initial attack accompanied by indignation and calls for revenge on both sides.
In an attempt to thwart or at least identify and manage fake content, a number of technology firms, including Adobe, have created watermarking solutions for recognizing AI-generated content. Google has introduced its own metadata-based content marker, SynthID, which can flag content as AI-generated. A recent article in Wired, Researchers Tested AI Watermarks—and Broke All of Them, described the difficulty of fighting digital fakes but concluded the fight must go on.
Adobe initially introduced its Content Credentials feature in 2021 and released it in the Photoshop beta the following year. Content Credentials are also integrated into Firefly, Adobe’s generative AI art model, and are automatically embedded in artwork produced using Firefly.
Those techniques are additive and can be circumvented and fix the date of the image. Many of the fake images from Israel were real images but with fake labels.
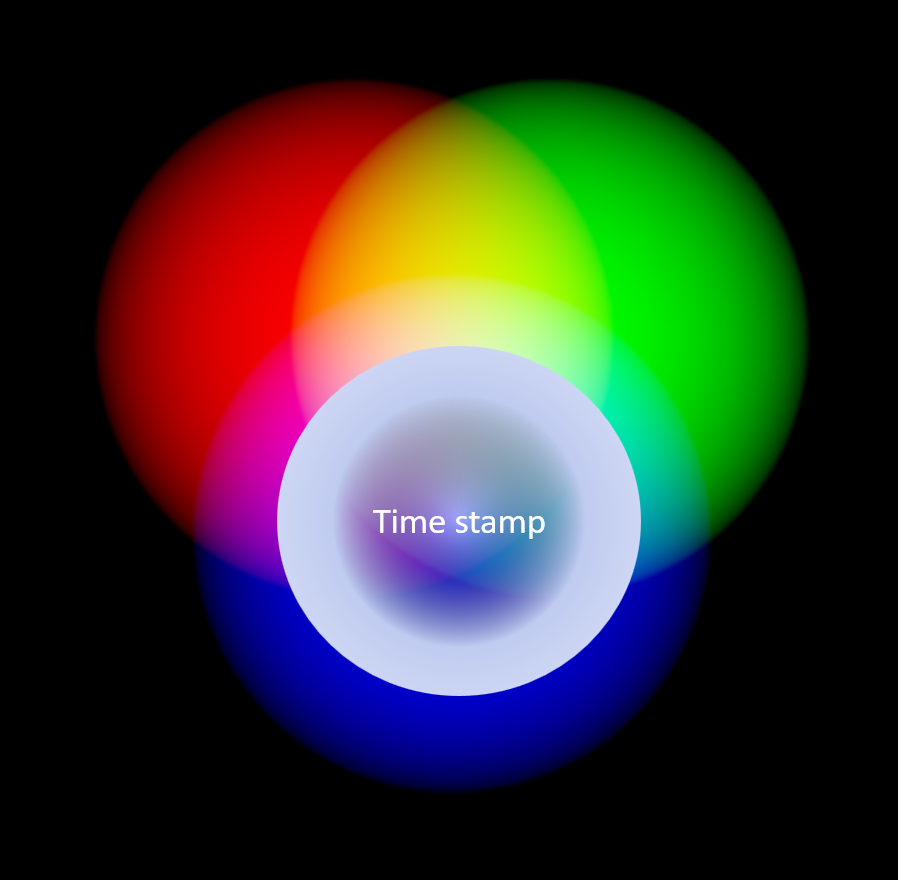
I propose embedding a system time stamp into each pixel at the time the pixel is created for the first time. We would then go from RGB to RGMT, in the pixel, not meta data or a header. And each and every pixel would be locked in a time stamp so if the images were doctored in anyway, whatever original pixels were left would tell the story. A simple comparison test could be run on an image to determine if all the pixels had the same time stamp—maybe something like a parity check.
The pixels must be indelible and if any attempt is made to alter any of the RGBT values, like Mission Impossible, the pixel self-destructs. If an image is being edited, it gets two T values, original and last (RGBT1T2).
Of course, the T value has to be encoded and only the originator of the image has the key.
Memory space permitting the originator’s name, or initials, could also be embedded.
The pixel gets bigger: 10×10×10×10, but with the 10-bits of the T, the value could include date and author.
VESA should be the organization to handle this with oversight from IEEE, ACM, and SID. Maybe Khronos too, since the API will have to be involved.
Sadly, it can’t be backward compatible but would be a firewall going forward.
Imagine—image integrity.